** MENU **
👀🔥 attacks
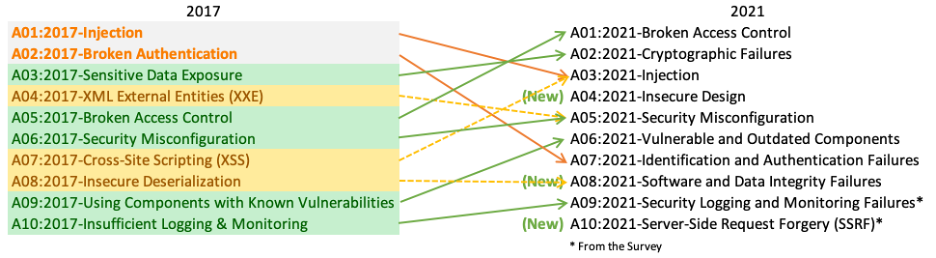
🔥 OWASP Top 10 🔥
| attack | mindmap | article | video | |
|---|---|---|---|---|
| CORS | securityzines | portswigger | ||
| Domain Lowering | securityzines, SOP | |||
| H2C smuggling | securityzines | portswigger | ||
| HPP | securityzines | |||
| HRS | securityzines | |||
| IDOR | securityzines | portswigger | ||
| LFI | securityzines | portswigger | ||
| RFI | securityzines | |||
| SQLi | securityzines | portswigger | ||
| SSRF | portswigger | |||
| SSTI | securityzines | portswigger | ||
| XSS DOM | iocscan | portswigger | ||
| XSS stored | securityzines | portswigger | ||
| XSS reflected | securityzines | |||
| XSRF | securityzines | portswigger | ||
| XXE | securityzines | portswigger |
👀🕶️ rotate-ip
# set the proxy ip rotator
curl https://raw.githubusercontent.com/TheSpeedX/SOCKS-List/master/http.txt -o http.txt
docker run --network host -it mubeng -a localhost:8089 -f http.txt -r 10 -m random
👀🧠 status-code
👀🧠 tools
- /tool/burp.png
- /tool/burp-extensions.png
- fireprox
- IP rotator TOR
- IP rotator for Burp
- nuclei templates
- dump elastic
- waf bypass
# run waf-bypass
docker run --network host -it 7209816c0627 --host='contoso.com' --proxy='http://localhost:8089'
# to select one payload we need to exclude all others
--exclude-dir='FP' \
--exclude-dir='API' \
--exclude-dir='CM' \
--exclude-dir='GraphQL' \
--exclude-dir='LDAP' \
--exclude-dir='LFI' \
--exclude-dir='MFD' \
--exclude-dir='NoSQLi' \
--exclude-dir='OR' \
--exclude-dir='RCE' \
--exclude-dir='RFI' \
--exclude-dir='SQLi' \
--exclude-dir='SSI' \
--exclude-dir='SSRF' \
--exclude-dir='SSTI' \
--exclude-dir='UWA' \
--exclude-dir='XSS' \